The importance of a WAF in Modern Cyber Security : Shielding Against Attacks
Enhancing web security in a connected world
What is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a security system that monitors, filters, and blocks HTTP traffic to and from a web application. It's designed to protect web applications from various attacks, such as cross-site scripting (XSS), SQL injection, and other common threats by analyzing HTTP requests and responses. WAFs operate at the application layer of the OSI model, helping to safeguard web applications from vulnerabilities and unauthorized access.
How it works :
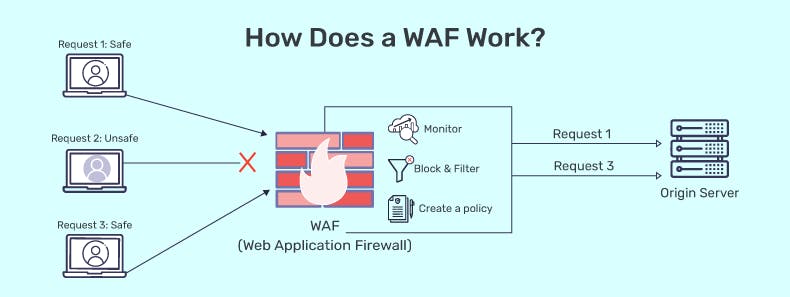
A Web Application Firewall (WAF) works by intercepting and analyzing HTTP/HTTPS traffic between a client and a web application. Its operation involves several key steps:
Traffic Inspection: The WAF examines incoming and outgoing HTTP requests and responses, scrutinizing the data packets for potential threats and vulnerabilities.
Rule-Based Filtering: It applies a set of predefined rules or policies to the incoming traffic, checking for patterns that match known attack signatures or behaviors.
Anomaly Detection: Some WAFs use behavioral analysis and machine learning algorithms to identify abnormal patterns or behaviors that might indicate a potential threat, even if they don't match known attack signatures.
Blocking and Filtering: When a threat is detected, the WAF can take various actions, such as blocking the malicious request, redirecting it, or triggering alerts for further analysis by security personnel.
Logging and Reporting: WAFs typically log all traffic and security events, providing detailed reports and logs for analysis, auditing, and compliance purposes.
Continuous Updates: Regular updates to the WAF's rules and threat intelligence ensure it remains effective against new and evolving threats.
By inspecting, filtering, and acting upon incoming traffic based on predefined rules and behavioral analysis, a WAF helps mitigate the risk of various attacks, safeguarding web applications from potential vulnerabilities and unauthorized access.
Purpose of Web Application Firewall :
Security Enhancement: Protects web applications from common vulnerabilities and attacks like SQL injection, cross-site scripting (XSS), and other OWASP top 10 threats.
Traffic Monitoring: Monitors and filters incoming and outgoing HTTP/HTTPS traffic, analyzing requests and responses for potential threats.
Prevention of Data Breaches: Helps prevent unauthorized access to sensitive data by blocking malicious traffic attempting to exploit application vulnerabilities.
Compliance Adherence: Assists in meeting regulatory compliance standards (e.g., PCI DSS, GDPR) by providing an additional layer of security for web applications.
Mitigation of DDoS Attacks: Some advanced WAFs also offer protection against Distributed Denial of Service (DDoS) attacks by recognizing and mitigating volumetric attacks targeting web applications.
Application Performance Optimization: Can assist in optimizing web application performance by caching and accelerating legitimate traffic while blocking harmful requests.
Real-time Threat Intelligence: Utilizes threat intelligence feeds and patterns to proactively identify and block emerging threats.
Types of Web Application Firewall :
Web Application Firewalls (WAFs) can be categorized based on their deployment methods and detection techniques. Here are the main types:
Network-Based WAF: Positioned between the internet and the web server, it inspects incoming and outgoing traffic. It's typically a hardware appliance or a software solution installed on-premises.
Host-Based WAF: Installed on the web server itself, this type of WAF monitors and filters traffic directly at the server level. It's software-based and operates within the server environment.
Cloud-Based WAF: Hosted and managed in the cloud by a third-party provider, this WAF doesn't require on-site hardware or software installation. It protects web applications by filtering traffic before it reaches the server.
Behavioral WAF: Utilizes behavioral analysis and machine learning algorithms to detect abnormal patterns and behaviors, providing protection against zero-day attacks and unknown threats.
Signature-Based WAF: Relies on predefined signatures or patterns of known attacks to identify and block threats. It's effective against known vulnerabilities but may struggle against new or modified attacks.
Hybrid WAF: Combines features of multiple types of WAFs, such as integrating both cloud-based and on-premises solutions or combining behavioral and signature-based detection methods for comprehensive protection.
Methods of Web Application Firewall :
Signature-Based Detection: This method involves comparing incoming traffic against a database of known attack patterns or signatures. When a match is found, the WAF takes action to block or mitigate the threat.
Behavioral Analysis: WAFs analyze the behavior of incoming traffic to detect anomalies or deviations from normal patterns. This method can identify zero-day attacks or previously unknown threats based on unusual behavior.
Whitelisting and Blacklisting: Whitelisting allows only trusted traffic based on predefined criteria, while blacklisting blocks known malicious sources or patterns. Both methods help in filtering traffic according to predefined rules.
Protocol Validation: WAFs inspect and validate incoming traffic to ensure it complies with the specified protocols (HTTP, HTTPS, etc.), rejecting invalid or malformed requests that could indicate an attack.
Machine Learning and AI: Some advanced WAFs leverage machine learning algorithms and artificial intelligence to continuously improve threat detection capabilities by learning from traffic patterns and behaviors.
Encryption and Decryption: WAFs capable of SSL/TLS inspection decrypt encrypted traffic to analyze its content for potential threats. This allows for thorough inspection while maintaining secure communication.
Content Filtering and Rewriting: WAFs can filter specific content types, such as blocking malicious scripts or sensitive data leakage, and even rewrite URLs or content to prevent attacks like SQL injection or XSS.
Rate Limiting and Session Tracking: By implementing rate limits on requests or tracking user sessions, WAFs can identify and mitigate attacks that involve excessive requests or abnormal session behavior.
Benefits of Web Application Firewall :
Enhanced Security: WAFs significantly bolster security by identifying and mitigating various threats, such as SQL injection, cross-site scripting (XSS), and other common vulnerabilities, protecting web applications from exploitation.
Protection from Data Breaches: By monitoring and filtering incoming traffic, WAFs prevent unauthorized access to sensitive data, reducing the risk of data breaches and leaks.
Regulatory Compliance: They assist in meeting regulatory standards (e.g., PCI DSS, HIPAA, GDPR) by providing an additional layer of security, aiding compliance efforts and avoiding penalties.
Continuous Threat Adaptation: WAFs are regularly updated with threat intelligence, allowing them to adapt and defend against evolving cyber threats and new attack vectors.
Reduced Downtime: By proactively identifying and blocking malicious traffic, WAFs help maintain the availability and reliability of web applications, reducing the likelihood of downtime due to attacks.
Improved Performance: Some WAFs optimize web application performance by caching legitimate traffic, accelerating load times, and filtering out malicious requests, enhancing overall performance.
User Trust and Reputation: By ensuring a secure online environment, WAFs enhance user trust, bolstering the reputation of the web application and the organization behind it.
Limitations of Web Application Firewall :
While Web Application Firewalls (WAFs) offer substantial security benefits, they also have some limitations and potential drawbacks:
False Positives: WAFs might sometimes incorrectly identify legitimate traffic as malicious, leading to false positives. This can result in blocking valid user requests, impacting user experience and functionality.
Complex Configuration: Configuring WAF rules and policies can be intricate, requiring expertise to fine-tune settings for effective threat detection without impeding legitimate traffic.
Resource Intensive: Intensive traffic inspection and analysis by WAFs can consume significant system resources, potentially affecting the performance and speed of web applications.
Limited Protection Against Advanced Threats: Some sophisticated attacks, especially those leveraging zero-day vulnerabilities or advanced evasion techniques, may bypass traditional WAF defenses.
Cost: High-quality WAF solutions, especially those offering comprehensive features and support, can be expensive to acquire, deploy, and maintain, posing a financial challenge for some organizations.
Maintenance and Updates: Regular updates and maintenance are crucial for WAF effectiveness. Failure to keep the WAF up-to-date with the latest threat intelligence could render it less effective over time.
Complexity in HTTPS Inspection: When inspecting HTTPS traffic, decrypting and re-encrypting SSL/TLS traffic can add complexity and potential security risks if not implemented properly.
How Web application Firewall implements ?
Assessment and Planning: Begin by assessing your organization's needs, understanding the web applications that require protection, and identifying potential threats and vulnerabilities. Create a plan detailing which applications require a WAF, considering their criticality and risk exposure.
Selecting the Right WAF Solution: Research and choose a WAF solution that aligns with your organization's requirements, considering factors such as scalability, performance, ease of management, and the types of threats it can effectively mitigate.
Deployment Strategy: Decide on the deployment method—cloud-based, on-premises, or hybrid—and establish a deployment strategy that integrates smoothly with your existing network infrastructure without causing disruptions.
Configuration and Customization: Configure the WAF according to your organization's security policies and the specific requirements of each protected application. Customize rules and policies to effectively filter traffic without impacting legitimate users.
Testing and Tuning: Conduct thorough testing to ensure the WAF operates effectively without causing false positives or blocking legitimate traffic. Continuously monitor and fine-tune the WAF's settings based on observed traffic patterns and security needs.
Integration with Security Operations: Integrate the WAF with existing security operations, such as SIEM (Security Information and Event Management) systems and incident response workflows, to enable quick incident detection, response, and remediation.
Training and Awareness: Train relevant personnel on how to manage and monitor the WAF effectively. Raise awareness among employees about the added security measures and the potential impact on their workflows.
Ongoing Maintenance and Updates: Regularly update the WAF with the latest threat intelligence, security patches, and software updates to ensure it remains effective against evolving threats.
Compliance and Reporting: Utilize the WAF's logging and reporting capabilities to generate compliance reports and audit trails, ensuring adherence to regulatory requirements and aiding in security audits.
Continuous Monitoring and Evaluation: Implement continuous monitoring of the WAF's performance, effectiveness, and the evolving threat landscape. Evaluate its efficacy periodically and make adjustments as needed to enhance security measures.
By following these steps, businesses can effectively implement a WAF to protect their web applications from a wide range of cyber threats while maintaining the integrity and availability of their online services.
Real-life examples :
Equifax Data Breach (2017): Equifax, a credit reporting agency, suffered a massive data breach where hackers exploited a vulnerability in a web application, gaining access to sensitive personal information of over 147 million individuals. Implementation of a robust WAF could have potentially prevented this breach by detecting and blocking the attack.
GitHub DDoS Attack (2018): GitHub, a software development platform, faced a powerful DDoS attack where traffic peaked at 1.35 terabits per second, making it one of the largest DDoS attacks ever recorded. GitHub managed to mitigate the attack and maintain service availability, largely thanks to its use of WAFs and DDoS protection mechanisms.
Magecart Attacks: Various e-commerce websites fell victim to Magecart attacks, where hackers injected malicious scripts into checkout pages to steal payment card details of customers. Implementing effective WAFs could have identified and blocked these malicious scripts, preventing the theft of sensitive financial information.
SaaS Application Security: Many Software-as-a-Service (SaaS) providers leverage WAFs to protect their applications. For example, Salesforce, a cloud-based CRM platform, employs WAF technology to safeguard customer data and prevent unauthorized access or manipulation of sensitive information.
API Security: WAFs play a crucial role in securing APIs. In 2019, a vulnerability in the Capital One banking app's API led to a data breach compromising the personal information of millions of customers. A robust WAF could have potentially detected and mitigated this API vulnerability.
In these real-life instances, the absence or ineffective implementation of WAFs resulted in security breaches and vulnerabilities, highlighting the importance of deploying and configuring WAFs to protect web applications and sensitive data from cyber threats.
Future trends for Web Application Firewall's:
AI and Machine Learning Integration: Increased use of artificial intelligence (AI) and machine learning (ML) to enhance WAFs' threat detection capabilities. This includes better anomaly detection, behavioral analysis, and adaptive learning to identify and mitigate evolving threats.
Cloud-Native WAF Solutions: Development and deployment of WAFs specifically designed for cloud-native environments, offering seamless scalability, integration with cloud services, and containerized security solutions.
API-Centric Security: As APIs become more integral to modern applications, WAFs will focus more on protecting APIs, offering specialized features and controls tailored for API security.
Automation and Orchestration: Integration of automation and orchestration capabilities within WAFs to streamline security operations, allowing for quicker threat response and adaptive mitigation.
Zero Trust Architecture Alignment: Aligning WAFs with Zero Trust principles, emphasizing continuous verification and authorization, thereby moving beyond perimeter-based security models.
Increased Emphasis on Behavioral Biometrics: Integration of behavioral biometrics within WAFs for user-centric security, leveraging behavioral patterns for improved authentication and access controls.
5G and IoT Security: Development of WAF solutions geared towards addressing security challenges posed by the widespread adoption of 5G networks and the expanding network of Internet of Things (IoT) devices.
Enhanced Compliance Support: Further development of WAF features to assist organizations in meeting evolving regulatory requirements and compliance standards across various industries.
Interoperability and Integration: Improved interoperability of WAFs with other security tools and platforms, fostering a more unified and effective cybersecurity ecosystem.
Quantum-Safe WAFs: Research and development efforts toward making WAFs resistant to threats posed by quantum computing advancements, ensuring resilience against future cryptographic challenges.
These trends represent potential directions for WAF technology, driven by advancements in cybersecurity, emerging threats, and the need for adaptive and proactive defense mechanisms for web applications.
Conclusion :
Hence, Web Application Firewalls (WAFs) stand as critical components in safeguarding web applications against a vast array of cyber threats. They play a pivotal role in ensuring the security, integrity, and availability of online services.
